Have you suddenly noticed strange redirects, unexpected content, or alerts from your browser that your site is unsafe? If so, your WordPress website may have been infected with malware. Website hacks can strike out of nowhere—potentially destroying your reputation, rankings, and user trust. But don’t panic! In this in-depth blog, you’ll discover how to remove malware from WordPress manually, step by step—no plugin required. Using proven strategies, real examples, and the industry’s safest practices, you’ll learn not just how to remove malware but keep it gone for good. If you want to roll up your sleeves and reclaim control of your WordPress site, keep reading.
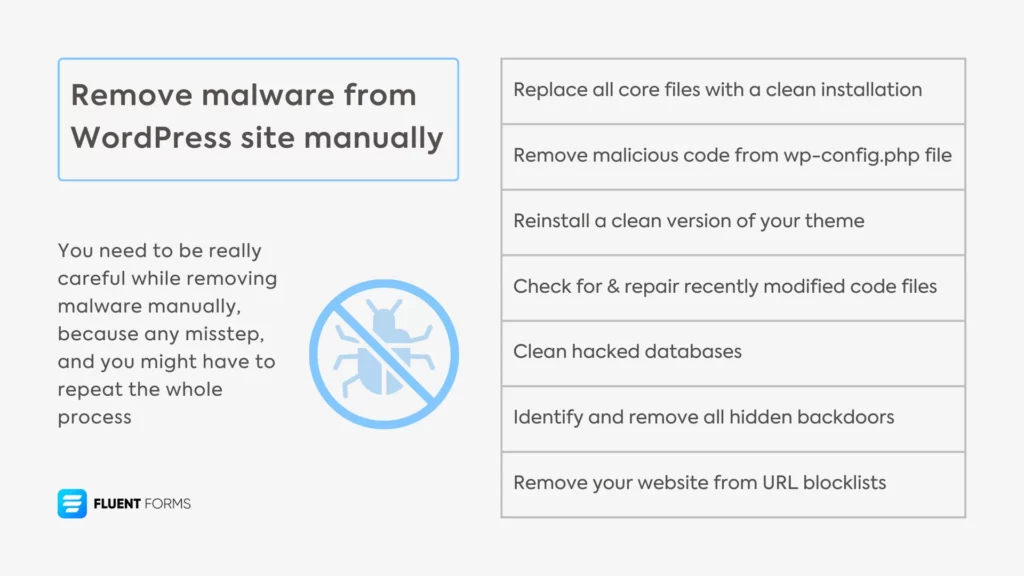
What is Manual Malware Removal from WordPress?
Manual malware removal from WordPress means eradicating harmful scripts, code, or vulnerabilities from your website by hand—without relying solely on automated tools or one-click plugins. Using this hands-on approach, you examine, identify, and clean every affected file and database entry, ensuring no malware remnants are left behind. While security plugins like Wordfence or Sucuri are helpful, a manual strategy is often necessary for deeply embedded malware or when plugins can’t catch sophisticated threats.

Malware in WordPress can take many forms, including backdoors, malicious redirects, spammy links, phishing scripts, and cryptojackers. According to Astra Security and Wordfence data, attackers commonly exploit outdated plugins, weak passwords, or unsafe themes. Manual cleaning helps ensure every angle is checked—from code to database entries—restoring your site’s integrity and search engine trust rapidly.
Why Manual WordPress Malware Removal Matters

Not convinced you need to learn how to remove malware from WordPress manually? Here are key reasons why this skill is crucial:
- Full Control: Manual removal lets you examine every corner of your site, guaranteeing deep cleansing.
- Bypass Plugin Limits: Not all malware is caught by automated scanners—especially zero-day exploits or new code variants.
- No Extra Bloat or Conflicts: Many plugins slow down your site or clash with themes. Manual fixes keep things lean.
- Better Learning: DIY removal teaches you about WordPress file structure, PHP, and web security best practices.
- Faster Site Recovery: Immediate action means less downtime, better SEO, and preserved brand reputation.
Examples: When to Remove WordPress Malware Manually

Still unsure? Here are real-world scenarios where manual malware removal in WordPress is essential:
- Redirection/Phishing Attacks: Your WordPress home or posts redirect to unrelated/casino/phishing sites.
- Admin Lockouts: Your account can’t log in, or new suspicious admin users appear.
- Injected Code in Core Files: You see unfamiliar code in
wp-config.php,functions.php, or at the top of theme files. - Google Warnings: Google Search Console or Chrome flags your site as “hacked” or “spreading malware.”
- Emails Sent From Site: Your server is blacklisted for sending spam emails via infected scripts.
If you spot any of these, it’s time to act fast and clean your site manually.
How to Remove Malware from WordPress Manually: Step-by-Step
Now for the heart of the guide—exactly how to remove malware from WordPress manually. Here’s the practical process trusted by security experts (as referenced by EasyWP, Hostinger, and more).
1. Backup Your WordPress Site
Before any cleaning, take a complete backup (files + database). Use FTP/SFTP or your hosting cPanel’s backup tool so you can restore accidentally deleted files if needed. Store this backup securely offline.
2. Scan Your Website Thoroughly
Use online scanners (like Sucuri SiteCheck), or connect via SFTP/FTP and search for modified files and unfamiliar code. Make a list of all suspicious files, recent changes, and newly created files. Focus on:
wp-config.phpindex.php.htaccess- Theme and plugin folders (especially
functions.php) - Uploads directory
3. Download Fresh WordPress Core Files
Download the latest clean WordPress zip from wordpress.org. Unzip it on your computer.
4. Replace Infected Core Files
Via FTP/SFTP, replace the following folders with fresh versions from the new download:
- wp-admin/
- wp-includes/
- All WordPress root files except
wp-config.phpandwp-content/
Do not overwrite your wp-content (themes, plugins, uploads), since this holds your website’s content.
5. Clean wp-config.php and .htaccess
Open wp-config.php and .htaccess in a text editor. Remove unfamiliar code, especially long code blocks, eval functions, or base64-encoded text. Replace .htaccess with default WordPress rules if unsure.

6. Review wp-content (Themes & Plugins)
Browse wp-content/themes/ and wp-content/plugins/. Delete any folders for themes/plugins you don’t use. Open functions.php in your theme and check for injected spammy code at the top or bottom. Reinstall any plugin or theme showing signs of tampering.
7. Purge Suspicious Files in Uploads
Explore wp-content/uploads/ for unexpected PHP, JS, or text files—these don’t belong there. Delete any non-media files and reset directory permissions to 755 (folders) and 644 (files).
8. Scan and Clean the Database
Access phpMyAdmin or a similar tool via your hosting dashboard. Search key tables like wp_options and wp_posts for suspicious iframes, JavaScript, base64/decode, or hidden admin users. Remove any malicious entries you find.
9. Change All Passwords & Update User Roles
After cleaning, reset passwords for all user accounts, FTP accounts, your hosting account, and your database. Check that only genuine admins exist in the wp_users table.
10. Re-Check, Harden, and Restore Reputation
Rescan your cleaned site with Sucuri or VirusTotal. Add define('DISALLOW_FILE_EDIT', true); to wp-config.php to prevent future in-dashboard edits. If flagged, request a review in Google Search Console to have malware warnings removed. Consider installing a lightweight monitoring plugin for peace of mind going forward.
Challenges, Myths & Common Objections
Despite its benefits, manual malware removal from WordPress faces a few challenges and misconceptions:
- Myth: Plugins Catch Everything
False. Automated tools often miss hidden backdoors or obfuscated code. - “I’m Not Technical”
With step-by-step guidance, most users can clean basic hacks. Extreme or repeated infections may require a WordPress security expert. - Fear of Data Loss
Proper backups make manual cleaning safe—you can always restore if something breaks. - Cleaning Once is Enough
If you don’t fix the root cause or update vulnerable plugins/themes, malware returns. - No Signs Means No Malware
Some malware hides quietly, waiting to strike. Continuous vigilance is key!
Frequently Asked Questions
What are the first signs of WordPress malware infection?
Common signs include strange redirects, spam popups, missing content, new admin users, slow site speed, Google warnings, or emails that your domain is blacklisted for spam.
Can I remove malware from WordPress manually without plugins?
Yes! Manual removal is possible for most infections. Follow our step-by-step process to scan, clean, and harden your site—just be sure to backup before making changes.
How do hackers usually infect WordPress sites?
Most hacks happen via outdated plugins/themes, weak admin passwords, nulled software, or vulnerable hosting environments.
Will Google remove the “this site may harm your computer” warning instantly after cleaning?
No—after you clean and secure your site, request a review in Google Search Console. Google typically rechecks your site within a few days.
Should I reinstall WordPress after malware?
It’s wise to replace all core files (except wp-content and wp-config.php). Do not delete uploads, but do reinstall plugins/themes if they were compromised.
Can malware come back after manual removal?
Yes, if the root vulnerability isn’t fixed. Always patch, update, and use strong passwords, and delete any unused themes/plugins.
What’s the difference between manual and plugin-based malware removal?
Plugins automate scanning, but often miss obfuscated code or backdoors. Manual removal is more thorough and ensures all traces are gone, especially for custom sites or recurring infections.
Is manual WordPress malware removal safe for beginners?
With careful backup and attention to steps, it’s safe for most. For complex hacks or lack of technical skill, consult a malware removal professional.
Will removing malware manually affect my search rankings?
Manual cleanup helps recover your SEO. Requesting a review on Google may speed up reindexing after you clean the site.
How often should I scan my WordPress site for malware?
At least monthly, or after every major plugin/theme update. Use a mix of manual checks and external scanners for best results.
Conclusion: Take Back Control with Manual WordPress Malware Removal
Malware attacks are scary—but learning how to remove malware from WordPress manually empowers you to act fast, minimize downtime, and reclaim your digital reputation in record time. Remember:
- Always backup your site before making any changes.
- Manually scan both files and database for suspicious code.
- Replace, clean, and harden every corner—not just core files.
- Update software, change passwords, and monitor continually.
With these steps, you’ll not only remove current malware but stop future threats in their tracks. Don’t rely solely on plugins—be the master of your own WordPress security. Ready to take action and keep your site (and visitors) safe? Get started today!
For more web security tips, WordPress guides, and actionable SEO strategies, check out our other blogs at Digital With Sandip!
